This week I needed to do some analysis of JIRA tickets that goes beyond the reporting JIRA provides – not entirely an uncommon task. My usual quickie toolkit for that purpose involves Jupyter notebooks, which I prefer over downloading CSVs and playing with spreadsheets because I can automate the notebooks given a JIRA API key.
In this case, though, I really want one of my PMs to be able to run these reports, and I don’t want to get into the whole “OK then type this at the command line” thing. The post title kind of gives this away, but after some thought I realized, hey, just check the notebook into the company’s GitHub and there we go.
But how about that API key? Obviously I don’t want to embed mine in the notebook. Is there some way to use GitHub secrets for this? Answer: yes, there is, and it’s really simple, but I don’t see it documented step by step anywhere else so I’m gonna do that here.
If you want the quick answer: GitHub makes secrets available as environment variables, and if you’re working in the GitHub Jupyter environment, you don’t need to do anything special with workflows to make that happen. Therefore, you can just use Python’s os.environ mapping object to get at secrets.
Here’s the step by step if you need it. I’m assuming you know GitHub and Jupyter on at least a basic level.
First, add the appropriate secret to whatever repo you’re using. If you’re not familiar with GitHub secrets, just go to the Settings for your repo (it’s the gear icon next to Settings), and in the left sidebar, click on Secrets, then Actions underneath Secrets. At the end of the clicking you’ll have something like this.
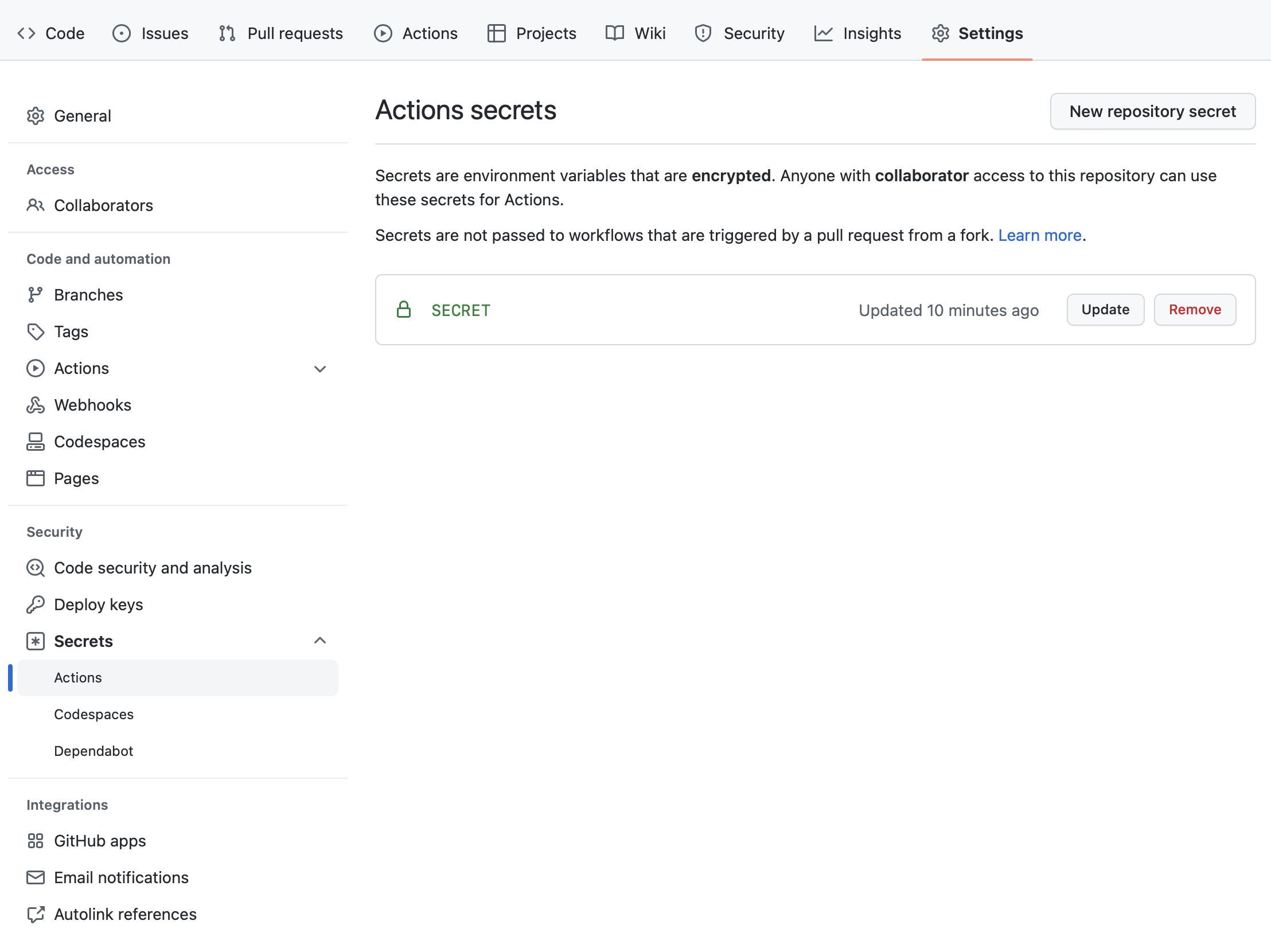
Click on New repository secret and add a secret. Maybe choose a better name than I did. Note that you can’t see the secret value once you’ve added it, as with any good secrets manager, although you can change it.
Now, I’m going to assume you’re using either Jupyter Notebook or JupyterLab; either works fine. I’m also going to assume you’ve cloned the GitHub repo locally. Once you’ve got all that squared away, and before you fire up your Jupyter instance, set an environment variable with the same name as the secret you just created. In my case:
SECRET="test secret"
export SECRET
Then run whatever you’re using to host your notebook, pop open the notebook, and write some code that looks something like this:
import os
secret = os.environ['SECRET']
print(f"Secret: {secret}")
os.environ is your magic incantation for getting access to environment variables. Unsurprisingly, that code produces this:
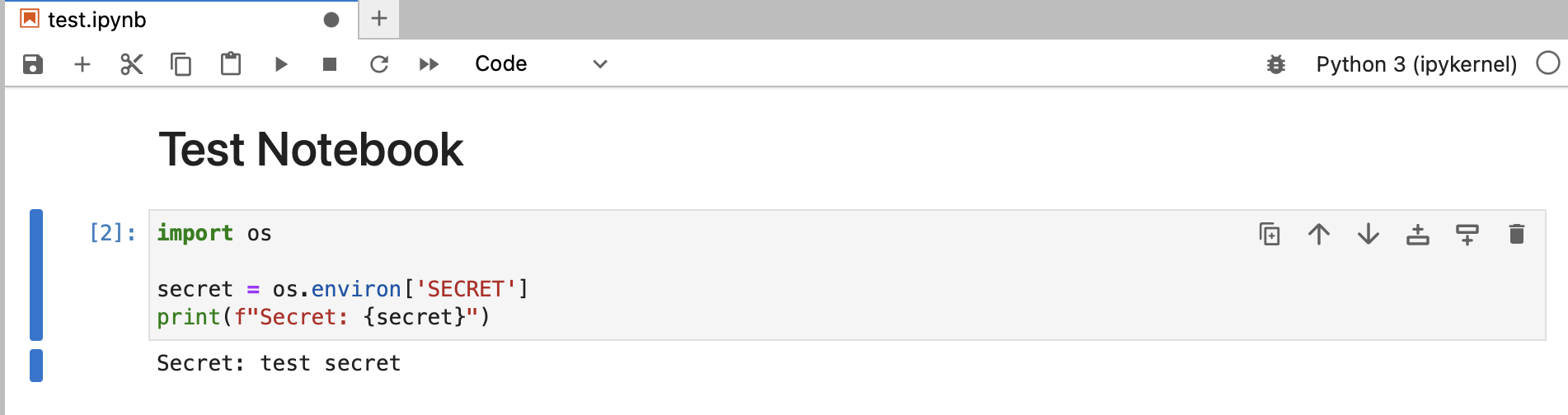
Uh, don’t actually use that code with a real secret. You wouldn’t want your secret to just get displayed like that.
OK. Security breaches aside, you probably see where this is going, especially if you read the summary up at the top. Save your notebook and commit it into the local repo, then push your repo back up to GitHub. GitHub runs Jupyter notebooks inline, so you can just go to the repo’s code page and click on your notebook and voila!
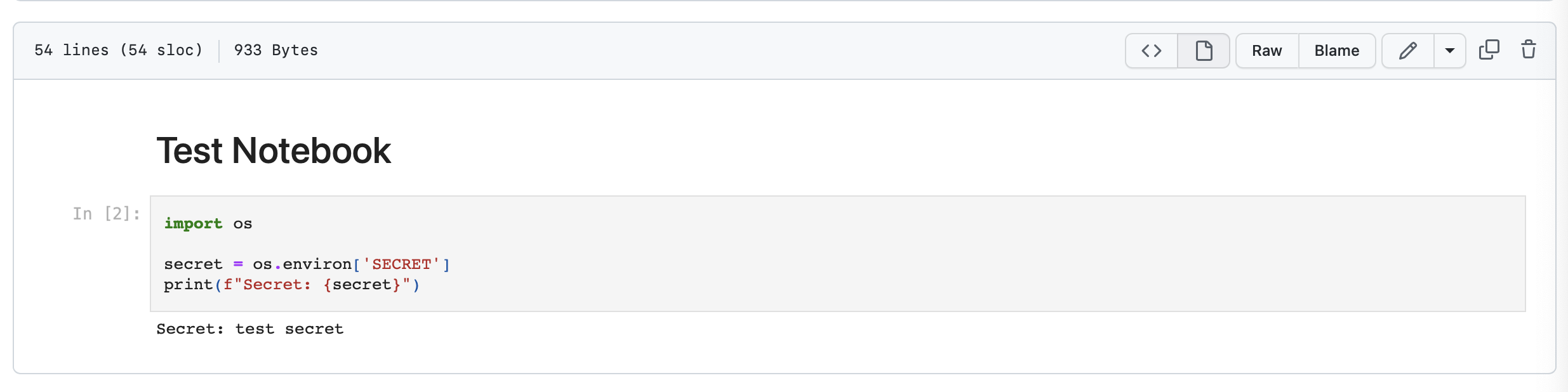
Yep, os.environ gives you access to secrets in the GitHub context. Isn’t that cool?
Side note: I embarked on this exploration for work purposes, but I did the research and testing on my own time. Thanks are due to Dipam Vasani, whose article on Accessing GitHub secrets in Python got me most of the way to where I needed to be.